Move to the Zero Trust Cybersecurity Model
The Zero Trust model takes a “never trust, always verify” approach, ensuring that each user and device is continuously verified and authorized, minimizing security risks and opportunities for successful attacks.
Victrix can help you implement the Zero Trust model and improve your security posture.

Benefits of the Zero Trust Model for Your Organization
At Victrix, we consider the Zero Trust model to be one of the most popular cybersecurity frameworks. It's the ideal solution for protecting critical systems and data.
1. Seamless user experience
2. Continuous auditing
3. Least privilege principle
4. Micro-segmentation
5. Monitoring and Analysis
6. Granular security policies
7. Dynamic trust
Contact us!
Do you have a question or a project? Do not hesitate to contact us!
"*" indicates required fields
By 2025, 60% of enterprises will use Zero Trust solutions instead of VPNs*.
Our cyber experts are available to answer your questions and guide you towards the best solution.
*Gartner statistics
Sensitive data identification
ZTNA Solutions Selection
Segmentation and isolation of the network, restriction of access
Least privilege data access
Continuous verification of confidence level
In-session traffic control
Data and application protection
Threat detection
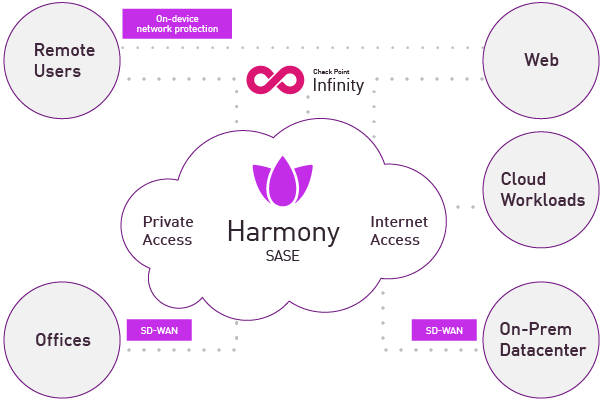
Discover Harmony Connect, Check Point's SASE Solution
Harmony SASE combines workplace security and network optimization in a single cloud-based platform designed for the modern enterprise.
Victrix, Your Strategic Partner for Continuously Improving Your Security Posture
If you have questions about protecting your cybersecurity or Zero Trust architecture, please contact us.
Our cybersecurity experts will work with you to implement the best solutions to keep your organization safe.